Wappalyzer is
unreliable*
*and it doesn't matter
What is Wappalyzer
If you've never heard of it, the Wappalyzer extension is a great tool that allows anyone to detect the technologies of a website.
Since it comes as a browser extension for popular browsers like Chrome, Firefox and Safari, it's always just a click away. All my web developer friends and I have made a habit of using it whenever we browse an interesting website. At a quick glance, you can learn that a website was built with WordPress, React, uses GSAP as an animation library and Google Analytics to collect user data.
If you have it installed on your system, go ahead and open it...
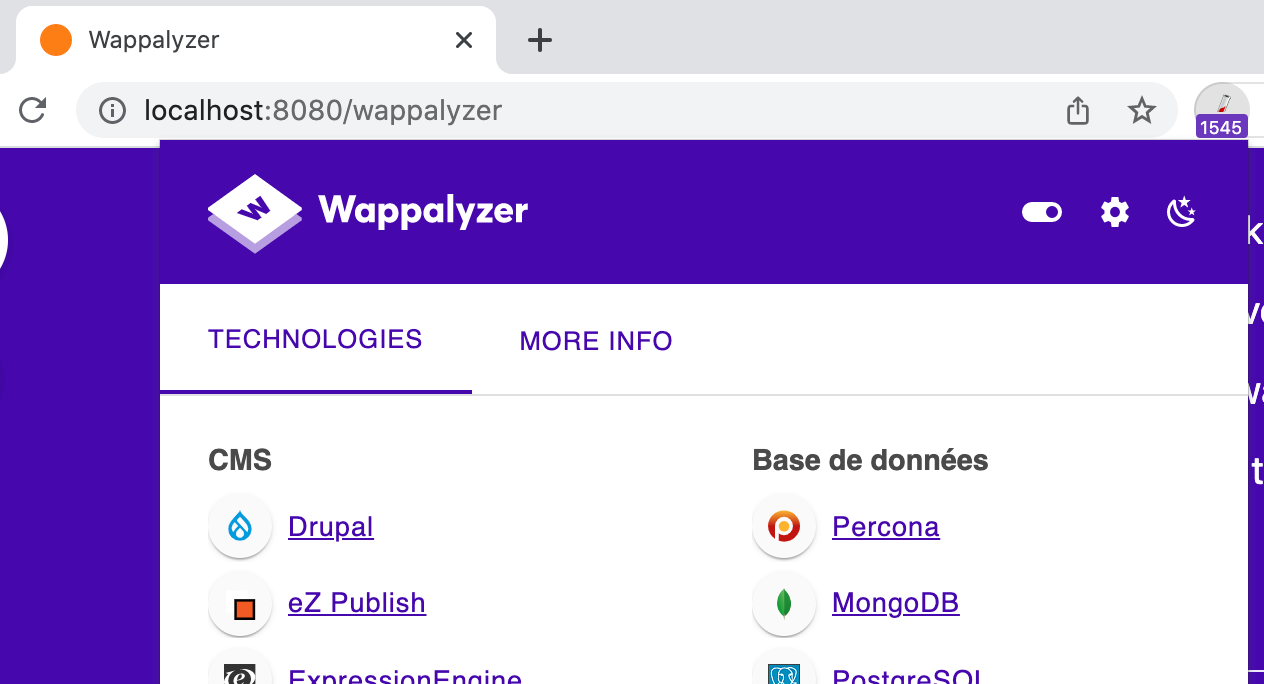
At the time of writing, Wappalyzer detects a whopping 1,929 technologies for this single webpage.
...what?? 😳 How come??
Having this much technologies leads to some interesting situations :
- ⚔️ – This site uses both React, AngularJS and Svelte, thus finally ending the framework war
- ✍️ – This site runs on WordPress, Drupal and a hundred other CMS, because choosing is renouncing
- 🤑 – Because having a performant website is cool, but money is cooler, I have 83 advertising platforms, 67 payment gateways and 177 e-commerce solutions running at the same time
- 💼 – I am fully invested in the Atlassian suite with both Atlassian Confluence, Atlassian Jira Issue Collector, Atlassian Bitbucket and Atlassian FishEye running. Typing HTML is serious business.
- 👴 – ...Oh, and a lot of jQuery stuff: jQuery, jQuery Sparklines, jQuery-pjax, jQuery Mobile, jQTouch, jQuery UI, jQuery Migrate and jQuery DevBridge Autocomplete.
Let me tell you how I was able to exploit the Wappalyzer Chrome Extension by reverse-engineering its inner workings.
How does Wappalyzer work?
Wappalyzer is open source. If you want, you can fork their GitHub repository and add your own technology to their list.
Every technology has a signature:
This signature can either be the source of a <script src="..."> tag, some variable in the global JavaScript scope window.$crisp = { ... } or the name of a cookie set on the page.
There are some more patterns that can be used to match a technology, the full list can be found here.
Once I knew how this tool worked, here's what I did:
- Download the full list of technologies from the Wappalyzer repository. They are divided into several JSON files available for download here.
- Parse each technology, get the regex used to match its signature.
- Use the awesome randexp library to generate a random string that matches each regex.
- Generate either a script tag, a cookie or create a variable with the informations obtained from the previous steps.
Here's an abridged version of the script used for this experiment. You can find the full version on my GitHub repository.
| import RandExp from 'randexp'; | |
| const technologiesGroups = [ | |
| { | |
| "WordPress": { | |
| "js": { | |
| "wp_username": "" | |
| }, | |
| "meta": { | |
| "generator": "^WordPress(?: ([\\d.]+))?\\;version:\\1", | |
| "shareaholic:wp_version": "" | |
| }, | |
| "scriptSrc": [ | |
| "/wp-(?:content|includes)/", | |
| "wp-embed\\.min\\.js" | |
| ], | |
| }, | |
| }, | |
| ]; | |
| const generateValue = (regStr) => { | |
| const reg = new RandExp(regStr); | |
| return reg.gen(); | |
| }; | |
| technologiesGroups.forEach((technologiesGroup) => { | |
| Object.values(technologiesGroup).forEach((technology) => { | |
| // Create cookie with key and generated value | |
| if (technology.cookies) { | |
| Object.keys(technology.cookies).forEach((cookieKey) => { | |
| const cookieValue = generateValue(technology.cookies[cookieKey]); | |
| const cookiePath = window.location.pathname; | |
| document.cookie = `${cookieKey}=${cookieValue};path=${cookiePath}`; | |
| }); | |
| } | |
| // Generate meta tags | |
| if (technology.meta) { | |
| Object.keys(technology.meta).forEach((metaName) => { | |
| const meta = document.createElement('meta'); | |
| meta.name = metaName; | |
| meta.content = generateValue( | |
| [technology.meta[metaName]].flat().join(' ') | |
| ); | |
| document.head.appendChild(meta); | |
| }); | |
| } | |
| // Add scripts with generated src | |
| if (technology.scriptSrc) { | |
| [technology.scriptSrc].flat().forEach((scriptSrc) => { | |
| const script = document.createElement('script'); | |
| script.src = generateValue(scriptSrc); | |
| script.type = 'javascript/blocked'; | |
| document.head.appendChild(script); | |
| }); | |
| } | |
| }); | |
| }); |
Should you stop using Wappalyzer?
This article specifically targeted Wappalyzer as it is the one I use and love, but all other tools on the market take a similar approach and suffer from the same shortcomings.
Should you stop using them because of this article? Absolutely not!
This was merely an exploration of how they work, how you can trick them, and have a bit of a laugh along the way.
Can you hide a website technology?
As you have seen, tricking them is actually quite easy and you could easily obfuscate what technology your website is using by manually altering the DOM and the global JavaScript scope.
At the server level, you could easily hide the php or nginx version by manipulating the HTTP headers sent with every request.
Since Wappalyzer has never been a threat to your business, you probably shouldn't delve into these kinds of practices because security through obscurity is never really viable in the long run.
In short, you could easily hide a website technology, but if you're using a vulnerable version of a specific software in the first place, you have bigger problems than trying to hide its version to your users.
The Web should be an open platform, what technology stack you use shouldn't matter as much as what you do with it.
I tweeted about this and had a fun exchange with the @wappalyzer Twitter account:
🥺
— Wappalyzer (@Wappalyzer) December 10, 2021
To rephrase my answer to the above Tweet, I think this short experiment is more of a statement of the quality of this tool than a rant about it. Being able to identify 2,000+ technologies is a lot, and I’m glad that a tool exists to be able to discover them.
(Note to prospective readers: I actually know and use some of these technologies. Not all of them, but enough to create beautiful web pages for my clients. If you want to be one of them, you can reach me at jverneaut@gmail.com.